Press Releases
This is the latest news on IGLOO Corporation. having been reported in press.
Significance of Network Partition Management from the Incident of Personal Data Leakage from Interpark
2016.11.15
2,137
“It was confirmed that your personal data has been leaked. The personal data that was leaked is as follows.” Late July, a huge security incident occurred in which personal information of 10.3 million members, which is 20% of the whole population, has been leaked from the internet shopping mall Interpark. The members of Interpark, thinking “Could it actually have happened?”, had to accept the fact that significant amount of personal information, such as telephone numbers and e-mail addresses, was leaked after checking Interpark’s messages.
According to the investigative results announced by ‘Private & Governmental Joint Investigation Group’ in late August, the attacker, who seemed to be from North Korea, penetrated into the company’s internal DB by sending a malicious e-mail to the employees of Interpark using Spear-Phishing. The attacker was hiding until he found the desired information, and finally showed up with the stolen personal information to attempt a financial dealing by asking for bitcoins worth KRW 3 billion to the Interpark.
On July 11, Interpark finally perceived the hacking 2 months after the initial attack when the attacker had asked for money. On July 13, Interpark filed a lawsuit to the police, and on July 25, they finally disclosed the fact that personal information had been leaked. Some users whose personal information had been leaked due to this incident filed a claim for compensation to the Seoul Central District Court based on insufficient measures to protect personal information and trying to evade responsibility by the Interpark.
What exactly was the problem for this incident? What is the reason security incident endlessly occur despite the investment and efforts by companies? Through the common problems of 3.20 cyberattack, KHNP hacking, and recently occurred Interpark personal information leakage incident, I would like to point out the fundamental problems, and try to find solutions.
Large Security Incident, What is the Problem?
There is a saying, “Nothing will come of nothing”. When there is a result, there is definitely a reason. Thus, there is a need to look at the cause so success will repeat and failure will not occur again. There is one common keyword that can be drawn from 3.20 cyberattack, KHNP hacking, and recently occurred Interpark personal information leakage incident. It is network partition.
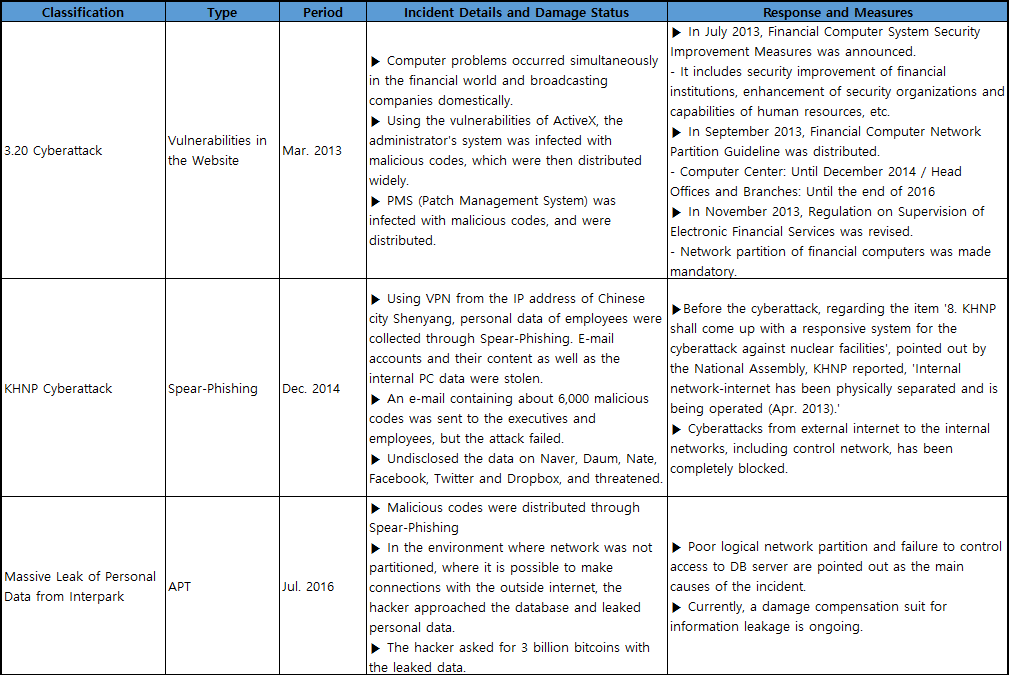
▲ Comparison Analysis of Damage Status and Measures of Cyberattacks, Source: Security Analysis Team of IGLOO SECURITY
If you look at the 3 incidents in the <Graph 1>, you can see that the cause of the incident and responsive measures after the incident are all connected to the network partition. First, you can check that after 3.20 cyberattack, network partition has emerged as one of the measures to fundamentally block leakage of important materials, and that network partition in financial computing has become mandatory.
KHNP incident, which occurred afterwards, is another case that the importance of operating network partition has emerged. Even though the company network, internet, and nuclear power plant control network have been physically separated for operation, internal information was leaked due to one of the employee’s PCs being infected by malicious codes.
Furthermore, the recently occurred Interpark personal information leakage incident also has some kind of relation with the previously mentioned 2 incidents. It was pointed out that insufficient logical network partition was the fundamental cause of the incident. According to the analysis results of Interpark hacking incident announced by the Ministry of Science, ICT and Future Planning (MSIP), and Korea Communications Commission (KCC) on August 31, the attackers were after the fact that Interpark applies logical network partition, in which the corresponding server is virtualized, only when the database administrator (DBA) connects to the DB server containing personal information, and stole the information outside.
Looking back at the series of cyberattack cases, you can check that network partition has been introduced more and more, but security threat that goes around network partition is also advancing day by day. Accordingly, I would like to discuss what network partition is, how security threat against network partition happens, and how to respond to it.
Types and Characteristics of Network Partition
Network partition refers to separating intra-network, which is used for work, and external network connected to the internet, so the intrusion from outside could be blocked and leakage of internal information can be prevented. Network partition is roughly divided into two: One is ‘physical network partition’ using 2 PCs, and another is ‘logical network partition’ using 1 PC, but network is divided through virtualization. Logical network partition is again divided into ‘SBC(Server-based Computing)’ and ‘CBC(Client-based Computing)’ depending on the base of virtualization.
Physical network partition is using one PC to connect to internet for external businesses, and the other for internal work without connecting to the internet, which has advantage of excellent security and safety. However, extra cost occurs due to constructing a separate network and the additional equipment such as PCs, and there is a concern that information can be leaked or be infected with malicious codes through secondary storage devices out of convenience or malicious intent.
Logical network partition dividing company network and internet with 1 PC has the advantage of being able to use existing equipment, but harder to manage compared to physical network partition. Server-based SBC method is a method to operate virtual PC at the server and the user connect to the PC as a client, so centralized management is possible, but the disadvantage is that since huge network traffic occurs, it takes budget to build server farm, and traffic load can occur. Furthermore, you need to take extra caution in firewall policy setup error or infection with malicious codes through terminal server storage.
Client-based CBC method is applying virtualization technology to the existing PC, so you can only use internet in the virtual region. Its characteristic is that cost could be minimized in building a network and introducing a new system compared to those of other methods. However, the PC environment differs for every user, so it is harder to manage, and when information is transferred between company network and internet, introduction of additional security solution is required.
Network Partition, Never Trust 100%…What are the Major Security Threats That can Occur in the Network Partition Environment?
Many companies think that if they apply network partition, they could be safe from security threats. If you introduce network partition, the security level of the companies does indeed get higher, but it does not mean that it is safe from all security threats. Various vulnerabilities could occur in the technological sector in building the environment as well as management and operation aspect where insiders are involved.
The security threat that can occur in the network partition environment can be roughly divided into 4 categories. First, the point of contact which inevitably occur due to the movement of data between company network and internet is abused as the path of attack.
For example, when security check was performed in the SBC-based network partition environment where the user can use the work environment through the virtualization server from the user’s local environment including the internet, a vulnerability has been found that work data in the virtual environment, which includes personal information, can be transferred to the user’s PC, which is connected to the internet, using shared directories or backdoor to go around the file transfer limit.
Second, handling exceptions regarding the data transfer between the networks is another factor that can cause security threat. Even after network separation environment has been built, due to the policy and work issues, the cases where exception handling is needed occur frequently. In this case, if the clear guidelines for transferring data in consideration of security level of data, and user authority have not been prepared, it might be possible that indiscriminate data transfer may occur. The main example of this is when the outsourced manpower transferred the data composed in the intra-network to the internet without any restrictions.
Third, you need to also pay attention to the security issues on hypervisor, in which multiple OS are executed and managed simultaneously by the host computer. When building server-based virtualization environment based on hypervisor, security vulnerabilities that could approach the memory in the virtual environment is the major example. For example, when resource and memory allocation for the virtual environment is handled using ‘Xenpwn’, which is hardware-based Xen hypervisor, it has been revealed that from the Xen hypervisor management domain, you can approach all the memories in the virtual environment.
Lastly, you must also pay attention to the unexpected security threat that can neutralize the network partition environment. The major cases are, using speaker microphone to leak files existing in the closed network by going around network partition, or using the EMR, which is emitted from network partitioned PC and devices, for the memory bus of the PC to transmit data through the smartphone using the frequency of the smartphone.
Safe Network Partition, How can We Achieve It?
Network partition can be counted as responsive measures to lower probability of attack to the important information of the companies by improving the security of internal networks, but you can see that it is not an absolute answer to block all cyberattacks. Since network partition does not guarantee perfect security, what efforts do you need to make to strengthen the security of network partition environment?
First of all, sending and receiving data between company network and internet should be efficiently controlled. The companies should manage the log occurring when data are sent and received between the networks, and must thoroughly inspect whether the data are transferred from company network to outside according to appropriate approval procedure.
Furthermore, since movable storage media is frequently used for the convenience of the work, media control or data leak prevention solutions should be additionally introduced to restrict the actions that violate network partition security operation guidelines. In addition, when transferring data that require high level security to outside, it is desirable to minimize file transfers by making them receive approval from security officer or higher responsible officer.
In particular, PMS (Patch Management System), which manages the security updates of major infrastructures in a batch from the center, remains as a possibility to be abused as the path of the attack, so it is recommended that PMS be installed and operated for each network. In reality, when e-mails on the internet is moved to company network through the data transfer system between the networks, the malicious codes attached to the e-mails are frequently introduced to the company networks.
In addition, continuous monitoring on permitted exception handling actions is also essentially required. The companies need to regularly inspect whether appropriate exception handling is being performed in accordance with the importance of the information included in the data, or authority of the insider. For example, when a certain user requests ‘writing authority’, the rank of the user concerned and relevance to the work must be considered, and only allow usage within the limited time. Also, after exception handling period is over, you must check if ‘writing authority’ is being used, so exception handling subject should be minimized when managing.
Furthermore, since various technology to go around network partition is actively being researched, it is necessary to prepare measures to minimize the damage from the attack by introducing security solution and executing recent security patch, which are compatible with network partition environment.
Continuous Network Partition Management, Introduction of Additional Security Solution is Necessary
We have examined security issues in the network partition environment, which is the recent topic. While cyber terrorism has become even more intelligent and massive scale security incident is occurring successively, many corporations and organizations are trying to introduce network partition, in which internet and company network is separated. In the financial sector, which needs to build network partition environment mandatorily in accordance with ‘Financial Computer Network Partition Guidelines’ by Financial Supervisory Commission (FSC), it is especially fast in introducing network partition, and SCADA, which is operated under closed network, is also considered as a field where it is very effective to introduce network partition.
However, if you want to increase the effect of introducing network partition, you must be aware in advance that network partition is not a cure-all to solve all the security problems. Even if internet and internal network is separated, the work must be done by moving back and forth between the two networks, so there is always a possibility that a hole could occur in those points of contact. In other words, unlike the original intention to block intrusion from outside and prevent information leakage from inside, it could be abused as a path of attack.
To complement these vulnerabilities, you must move forward one more step from building a network partition environment to back up with complement measures to effectively control data transfers between the networks, and observe and analyze in real time the security threats that can go around network partition environment. Finally, it is my strong wish that you do away with the lackadaisical thought that network partition would block all the security threats, and raise the security of network partition environment by establishing a clear data transmit policy and introducing additional solutions.


